In the last two years, digital commerce and remote work demands have created new opportunities and security risk vulnerabilities. As a result, the digital workforce and consumers require more access to digital assets (data, applications, intellectual property, systems, etc.) from multiple devices, sources, and locations. At the center of securing these digital interactions, enterprise organizations must ensure that appropriate – versus unlimited – access is granted only to trusted user identities.
This transformation drives a new paradigm known as “identity-first security,” which focuses on the integrity of the user identity as the core of an organization’s security strategy. This approach is designed to ensure that the individual is authorized throughout the user’s digital journey and granted the right level of access to the appropriate digital assets. Whether access is over the cloud or on-premises, identity-first security is now a prerequisite for Zero Trust architecture.
The missing piece to the Zero Trust equation, in many scenarios, is an authorization framework to determine who has access to what information and when.
Authorization has roots in identity and access management (IAM) and has been a foundational component of IAM platforms for decades. The advent of the “Digital Age” fueled both the explosive growth of data and the exponential rise of new security risk vectors threatening modern computing environments. Thus, there is a rapid convergence between traditional IAM, cybersecurity, and data protection, including privacy requirements.
This evolution is driving the re-emergence and relevance of authorization and the subsequent need to create, manage, and enforce authorization policies in a simple, user-friendly manner. Legacy approaches such as role- and attribute-based access control (RBAC and ABAC) are common and continue to be capable methodologies of policy creation. However, policy-based access control (PBAC) has emerged as the more effective authorization policy creation and management approach. This is due to its user-friendly GUI and its policy-based approach to constructing policy logic, eliminating the need for technical and coding expertise requirements to create and manage authorization policies. Powered by PBAC, authorization is manageable by everyone, including business owners and data analysts.
Organizations now seek to leverage the PBAC framework to support the demands that modern computing environments require with respect to balancing frictionless digital user journeys, security risk mitigation, and data privacy.
To gain further insight into market trends and security pain points and validate the identity-first security shift, PlainID interviewed more than 200 industry respondents, including managers and C-level IT, and security professionals in the U.S., Canada, and the U.K., all working for companies with more than 2,000 employees. We asked them for their views on the need for authorization and access controls and discovered three key findings
Key finding 1: Authorization has become the top priority in IAM
IAM priorities are shifting this year, with authorization-related initiatives such as run-time access, API access control, and PBAC gaining traction.
The C-suite is driving this demand, ranking authorization initiatives at the highest levels, with run-time access at 62 percent, API access control at 51 percent, and PBAC at 43 percent. And they’re putting money behind this need, with an average of 21 percent of their IAM budgets allocated towards authorization. This allocation is consistent across all company sizes.
This data indicates that authorization is top of mind for high-level decision-makers and that authorization-related topics are a strategic priority for the 2022 organizational roadmap. We see the same trend and priorities when comparing 2023 and beyond, showing those topics to be mid-to-long-term strategic priorities.
Key finding 2: Organizations are consolidating and standardizing access control and authorization
Managing access has become more complex, manual, and distributed across multiple systems as the industry shifts to identity-first security. The security perimeter spreads across data, APIs, applications, and more.
This complexity drives the need for standardization and scale, which were reported as the top two drivers for adopting authorization solutions, at 25 percent and 17 percent, respectively. Creating a standard approach is more important than ever—one that spans all modern enterprise architectures and includes access control to data, APIs, and the cloud infrastructure itself.
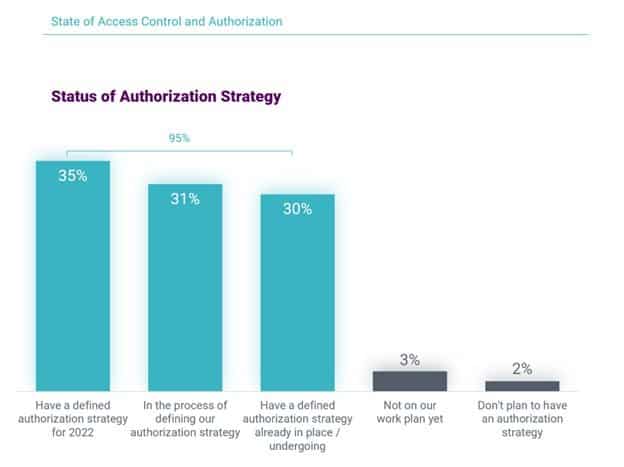
Key finding 3: Most companies already have or are working on their authorization strategy
Of the professionals surveyed, 95 percent are well down their paths to an authorization strategy. There was some differentiation in the level of strategy maturity. Respondents are almost equally split in terms of where they are on the authorization roadmap – 35 percent already have an authorization strategy in place, 31 percent have defined their strategy and are ready to implement it in 2022, and 30 percent are in the process of determining their strategy, with plans to implement over the next five years. Only 2 percent didn’t have plans to implement an authorization strategy.
As more organizations navigate their employees working from offices and homes, the landscape of risk vectors will only increase. Threat actors have recognized that targeting identities can be a vital access point. As a result, authorization will become more critical to protecting people, networks, and data.
In addition to strengthening their security posture, organizations will implement authorization solutions for standardization, scalability, and visibility. This is no surprise as the enterprise perimeter becomes more distributed and the proliferation of applications, data, APIs, and clouds. Subsequently, organizations are looking for scalable solutions to manage access policies across different resources.
Wherever digital assets are kept, security isn’t complete until organizations can confidently grant the authorized user access to the permitted digital assets in a dynamic and real-time manner. In this age of cloud-based collaboration, exploding data growth, and work-anywhere environments, authorization is needed to complete any organization’s security picture.
Source: CPO Magazine