Ever since the Internet of Things (or IoT) became mainstream, this technology has continued to enthrall us in almost all business landscapes and aspects of our daily lives.
From health trackers and smart appliances to autonomous delivery vehicles and AI-enabled interactive packaging — IoT is the bedrock to connect devices with users and organizations, generate data and enable more intelligent experiences.
However, companies looking for IoT development services in some form or the other have a major challenge in front of their eyes, i.e., ensuring data privacy for end-users. That is where the concept of IoT security gains precedence.
What is it exactly?
Simply put, IoT security is the practice that helps businesses keep their IoT systems safe. Using its network, sensors, and analytics, IoT offers the core tools to automate data collection and transmission between physical objects and generate insights.
Building trust in IoT connected devices
When the IoT technology came into the picture in 1999, little did anyone know that it would convert the fabric of the world into a smarter and more responsive one, conveniently merging the physical and digital universes.
However, not having clarity about security best practices and associated expenses keep many businesses from hopping on the IoT bandwagon. In fact, research shows that 90% of consumers lack confidence in IoT device security.
Understanding IoT security risks
Modern IoT ecosystems are complicated. Machines, devices, sensors, and servers are connected and configured to transmit data over cellular networks.
Since IoT devices deal with volumes of data, it makes them prone to data breaches and threats. IoT security tools ensure the integrity and confidentiality of the IoT network, especially if it scales and expands geographically.
Types of IoT security tools for networks and devices
When it comes to IoT devices, their protection requires a matrix of detection, prevention, and mitigation solutions across various layers. Let us check out three essential security tools:
1. Sophisticated IoT protect products
These protection agents assess the hacking risk in the IoT devices and instantly alert the admin besides blocking potential phishing and malicious intent before it is too late. They offer on-device runtime protection.
Features:
- Review all the unmanaged IoT devices in your network, and note and highlight their risks hassle-free.
- Block all forms of cyberattacks by applying real-time IoT threat intelligence and virtual patching.
- Implement zero-trust policies for preventing unauthorized lateral movement on and access to the IoT device.
These tools safeguard businesses against IoT network-and-on-device cyberattacks. IoT Protect Products cover them all, from medical devices and IP cameras to industrial controllers and smart elevators.
2. Industry-specific IoT protect solutions
Use these on-device runtime protection agents to deploy connected IoT systems with built-in security that keeps even the most sophisticated cyberattacks at bay.
This type of IoT security solution prevents IoT cyber-attacks across smart offices and buildings, healthcare, and manufacturing units. Since every organization and industry has a different security requirement, it is possible to tailor the product accordingly.
Features:
- Receive on-device runtime protection to alleviate all security risks.
- Deploy a 360-degree prevention-first strategy for your IoT network.
- Get access to real-time threat intelligence and review.
3. IoT protect firmware
This data security service for Industrial IoT gives on-device runtime protection to IoT devices, blocking malicious intents with zero-trust segmentation. Minimise IoT security challenges considerably.
Features:
- Prevent unauthorized access and malicious intent from landing on your IoT devices.
- Deploy zero trust strategies for saving IoT devices from getting infected due to unauthorized lateral movement and access.
- Auto-generate policies to minimize your risk exposure and save time otherwise spent on configuring policies manually.
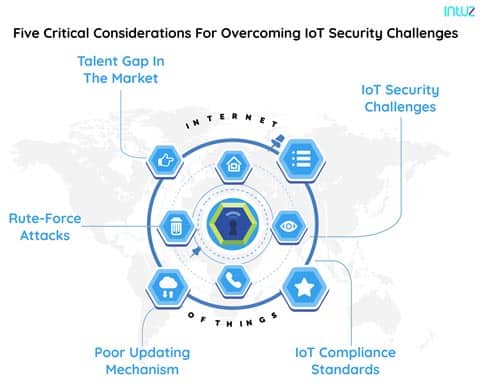
Five critical considerations for overcoming IoT security challenges
1. Ransom malware
As the number of connected devices rises, the extent to which ransomware is used to hack IoT devices has grown exponentially.
In a typical case of ransomware, the hacker locks users out of their devices and threatens to publish their personal data or perpetually blocks access unless a ransom is paid.
The best way to mitigate the problem is by segmenting data and critical networks from access by IoT devices and ensuring regular data backups.
2. Talent gap in the market
It is true the world of IoT has grown by leaps and bounds, but we still have a long way to go when it comes to offering top-notch IoT product development services.
There is a massive IoT skill gap in the market, and it is hindering businesses from tapping the full potential of the technology. That is why it is important to train and upskill programs for developers. The more knowledgeable your team members are in IoT, the more secure your IoT devices will be.
3. IoT compliance standards
Securing IoT systems and the data associated with them is essential as insecure IoT devices pose a vulnerable gateway to cyberattacks.
There has to be complete agreement with all stakeholders that the data is kept secure. To ensure that, you must establish dedicated compliance and privacy guidelines that redact and anonymize sensitive data.
For instance, cached data which is no longer necessary should be safely discarded. All web, mobile, and cloud applications used to access, process, and manage data associated with IoT should comply with these guidelines.
4. Poor updation mechanism
IoT products are designed keeping the ease of use and connectivity in mind. They may be secure when you purchase them, but the technology can become obsolete over time, making the products more vulnerable to security flaws. That is why it is essential to keep updating the IoT devices regularly not to become prone to data breaches.
5. Brute-force attacks
A brute-force attack consists of an attacker using trial-and-error to guess login info or find a hidden web page with the hope of eventually guessing correctly. This requires the hacker to systematically check all possible passwords and usernames until the correct combination is found. Brute-force attacks are also the most common form of cybercrimes.
Unfortunately, almost all IoT devices are vulnerable to password hacking because of weak login details. Therefore, there is a need to change the passwords periodically or install robust firewalls to safeguard the devices from getting compromised.
Best IoT security technologies
1. Antivirus, firewalls, and intrusion prevention tools by vendors like Darktrace and Cisco to secure the network connection between IoT devices and the backend systems on the internet.
2. Robust authentication mechanisms for users include digital certifications, biometrics, and two-factor authorization by Datacard, Baimos Technologies, and Gemalto.
3. Ensuring complete encryption key lifecycle management for a safer connection between backend systems and IoT devices with the help of the likes of HPE.
4. Data security analytics solutions to detect IoT-specific attacks and intrusions usually not identified by traditional network security tools. SAP, Indegy, and Kaspersky Lab excel here.
Over to you
If you are in the business of IoT, you must not take your users’ data security lightly. The risk is real every step of the way, with cyber hackers waiting to take advantage of an IoT network.
IoT security solutions will help detect network traffic bursts and outages and denial-of-service attacks and enable you to resolve the issues proactively without hampering user experience.
More importantly, such solutions provide a granular view into device behavior that safeguards the digital assets, thus building trust among your IoT users. Is that not the end goal?
Source: CPO Magazine






